Let’s Encrypt’s Certbot is a tool to secure the entire internet. If you have gone through the trouble of setting up a secure website, you know what a hassle getting and maintaining a certificate is. Certbot and Let’s Encrypt can automate away the pain and let you turn on and manage HTTPS with simple setup commands. It’s totally free to use.
It’s not required to use Let’s Encrypt to obtain an SSL, you have the flexibility to use any Certificate Authority you choose.
This is the tutorial to help you to install free ssl on ubuntu 20.04 Linux system.
Prerequisites:
- A running Ubuntu 20.04 system with non-root, sudo enabled user.
- A fully registered domain name pointed to the ubuntu 20.04 server.
- Server running engine Nginx or apache. (We will use Nginx for this tutorial)
- Ports 80(HTTP) or 443(HTTPS) must be opened on your server.
Note: Installation method is the same for Apache too, only the plugins used are different.
Free SSL on Ubuntu Server Using Certbot:
1. Installing Certbot
Snap package is the easiest way for installing Certbot on the Ubuntu system. Snap packages work on nearly all Linux flavors, but they required that you’ve installed snapd first in order to manage snap packages. Actually, Certbot is a third-party service that makes it easier to install Let’s Encrypt. First SSH to the server, update the repository server:
sudo apt update && upgrade -y
After the system has been successfully updated and upgraded, download services or packages that support(is required) the running of Certbot Let’s Encrypt.
sudo apt install certbot python3-certbot-nginx
Once done, confirm the Nginx Virtualhost configuration. The Nginx virtualhost is the one that guarantees success in installing Let’s Encrypt. And Certbot will check Nginx to generate SSL using Let’s Encrypt.
2. Nginx Virtualhost configuration
To create a Certbot SSL certificate, make sure the domain or subdomain is registered on the Virtualhost Nginx web server.
Open the file vim /etc/nginx/sites-available/your_domain.conf and edit server_name with your domain.
vim /etc/nginx/sites-available/your.domain.conf
...
...
server {
listen 80 default_server;
root /var/www/html;
index index.html index.htm index.nginx-debian.html;
server_name your.domain.com
return 404;
...
...
If server_name matches the target Let’s Encrypt is going to register. Test the Nginx service.
Nginx testing:
After the configuration has been saved, use the following command to check the status:
nginx -t
On correct configuration output will be:
nginx: the configuration file /etc/nginx/nginx.conf syntax is ok
nginx: configuration file /etc/nginx/nginx.conf test is successful
Restart the Nginx service:
sudo systemctl restart nginx
3. Allow HTTPS
You have to open ports 80 and 443, namely HTTP and HTTPS so that you can enter and exit the server through the firewall.
Check the firewall status:
sudo ufw status
If you have an inactive firewall, you skip to the next step. But firewall turn on is recommended since it protects the server from external attacks.
Now, add permissions for ports 80 and 443 i.e HTTP and HTTPS:
sudo ufw allow http
sudo ufw allow https
sudo ufw allow ssh
Then enable Firewall/UFW:
sudo ufw enable
check status:
sudo ufw status
The output will be:
Status: active
To Action From
-- ------ ----
80/tcp ALLOW Anywhere
443/tcp ALLOW Anywhere
244 ALLOW Anywhere
80/tcp (v6) ALLOW Anywhere (v6)
443/tcp (v6) ALLOW Anywhere (v6)
244 (v6)Finally, you can run Certbot and generate certificates.
4. Generate SSL
Since we’re using Nginx plugin we can create a certificate for DNS your.domain.com as:
sudo certbot --nginx -d your.domain.com
Which will create a certificate for the domain we are requesting, answer some questions for SSL. (email, agree terms, etc.) After that Let’s Encrypt SSL certificate will be generated in /etc/nginx/sites-available/ directory for your domain.
Output
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel):
The certificate is only valid for 90 days, we must renew the certificate every time it expires.The good thing is Certbot that has been installed already provides a service for updating scrips to cron-job (/etc/cron.d/).
sudo systemctl status certbot.timer
The output will be:
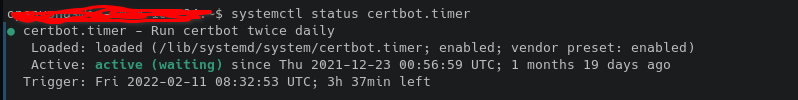
This command will run twice a day and will renew every 30 days from the expiration date.
Test the update and ensure the renewal process works:
sudo certbot renew --dry-runSaving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Processing /etc/letsencrypt/renewal/your.domain.com.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Cert not due for renewal, but simulating renewal for dry run
Plugins selected: Authenticator apache, Installer apache
Renewing an existing certificate
Performing the following challenges:
http-01 challenge for your.domain.com
Waiting for verification...
Cleaning up challenges
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
new certificate deployed with reload of nginx server; fullchain is
/etc/letsencrypt/live/your.domain.com/fullchain.pem
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Processing /etc/letsencrypt/renewal/your.domain.com.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Cert not due for renewal, but simulating renewal for dry run
Plugins selected: Authenticator apache, Installer apache
Renewing an existing certificate
Performing the following challenges:
http-01 challenge for your.domain.com
Waiting for verification...
Cleaning up challenges
If the automatic renewal fails, Certbot sends an error message to the email that was registered at the time of generating the certificate.
Encrypted keys for your custom domain will be stored in /etc/letsencrypt/live/your.domain.com/fullchain.pem and letsencrypt/live/your.domain.com/privkey.pem. Which can be used as certificate files to encrypt custom associated domains manually.
That’s it. You have successfully configured free SSL on Ubuntu server using Certbot and custom domain.
Thank you!
