JSON Web Token (JWT) is a compact, URL-safe means of representing claims to be transferred between two parties. The claims in a JWT are encoded as a JSON object that is used as the payload of a JSON Web Signature (JWS) structure or as the plaintext of a JSON Web Encryption (JWE) structure, enabling the claims to be digitally signed or integrity protected with a Message Authentication Code (MAC) and/or encrypted.
The above is an abstract given by the authors of JSON Web Token (RFC 7519).
JWT (pronounced as “jot”) is a way of transferring signed data between two parties. Also, the use case of JSON Web Token is seen in applications where authentication and information exchange is present. It is a JSON object that has been signed using a secret key or a public/private key pair. It also can have an expiration date after which the token is not valid to be used.
When to use It?
- Authorization JWT used for authentication is the most common cause. After the user logs in a signed JSON token containing userId and email is sent back as a response. After the login, each following request should be sent with JSON Web Token attached for the server to know that the user is authenticated. Mostly used in Restful APIs, where it follows a stateless approach meaning the server doesn’t know about the user that sent the request.
- Information Exchange It can be used as a secure form of information exchange between two parties. This way of using JWT is not as widespread as seen in the case of authorization. As this form of information exchange becomes expensive in terms of IO speeds on the server side. This is because encryption algorithms are slow, using symmetric algorithms can make it faster. It is seen in both parties who are exchanging information.
Benefits of using JWT
- Follows stateless architecture, making it easier for following different programming paradigm
- Easier for the backend as constant database lookup is not necessary to verify the user
Structure of JWT
JWTs look like strings of alphabets and numbers. There are three parts to it firstly the header, secondly payload, and thirdly signature.
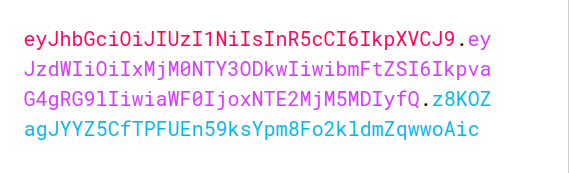
In the above jwt, the first part is the header which contains the algorithm used.
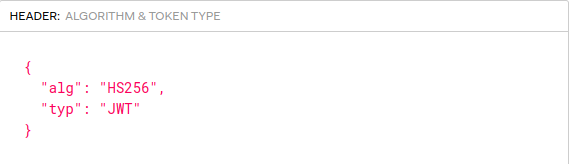
After the (”.”) separator the next part is the payload it contains the actual data and the iat tells the time that the JWT was issued and it must be a numerical number.
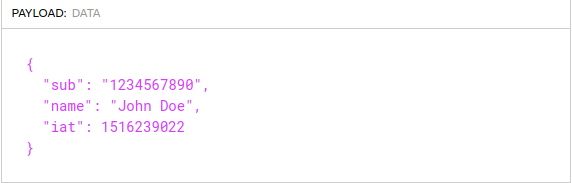
The last part is the verification signature. So, it contains the encoded verification signature that was used to sign the JSON object.
Conclusion
The article is a two-part look at JWT. The first part touched upon the theoretical section of It. Also, the next part of this article is going to look at how they are implemented in NodeJs.
